Setting up SPF for email deliverability
What is SPF?
SPF (Sender Policy Framework) is a way for Domain owners to “authorize” mail servers to send email on behalf of the domain. Receiving mail servers use SPF to verify that incoming messages that appear to come from your domain were sent by servers authorized by you. Creating a proper SPF record increases the chances of your emails ending up in an inbox instead of a spam/junk folder (or worse rejected).
Each domain is allowed to have a single SPF record in their DNS zone. The records look something like this:
v=spf1 include:salsalabs.org include:_spf.google.com ~all
The SPF record above has the following components
v=spf1 = This defines this record as an SPF record
include:salsalabs.org = Emails sent from the service Salsa Engage are authorized
include:_spf.google.com = Emails sent from Google are authorized
~all = If any emails NOT from an authorized server are received, you can do with them what you like (SoftFail)
How SPF works
An SPF record is analyzed by the receiving email system is that each entry in the record is examined and then “exploded” into its constituent IP addresses. These IP addresses are then compared to the IP address of the server that originated the email (note that this is the IP address of the server… not the email client). If the IP address of the sender’s server appears in the SPF list, then the email is considered to be coming from a source that is “approved” by the domain.
SPF does NOT mean that the receiving email system won’t think your email isn’t spam … only that it came from a server approved by the domain. Lots of spammers use SPF records. SPF is just another layer of protection that signals your
The DNS ten-lookup rule
During the SPF lookup process to convert record entries into IP addresses, there is a limitation (10) on the total number of DNS lookups that are permitted for performance reasons.
If your SPF record results in more than 10 lookups during that process, the receiving server will “give up” and stop processing the SPF.
Microsoft’s prior abuse of SPF lookups:
Microsoft Office 365 currently recommends an SPF include statement that looks like include:spf.protection.outlook.com .
This one include statement previously resulted in a total of 9 lookups which really limited the ability of Microsoft’s customers to SPF whitelist additional email providers.
As of 2020-11-15, it appears that the include:spf.protection.outlook.com statement now only results in a single DNS lookup which is fantastic.
Avoiding the ten-lookup limit for SPF records
If you run into an email provider that is abusing the SPF DNS lookup limitation and is putting your SPF record in danger of being ignored, you have a few options:
Subdomains - Look into splitting your email across multiple subdomains instead of having all your email come from the same domain.
Flatten your SPF record - See our article on Flattening your SPF record
Reorder your SPF - Put the most important (highest volume) SPF entries first in your record.
More tips for improving your SPF record to avoid the 10-lookup limit
https://help.returnpath.com/hc/en-us/articles/222479888-How-can-I-avoid-SPF-failures-if-I-am-reaching-the-DNS-lookup-limit-
Testing your SPF record
When you test an SPF record, there are really two steps:
Test to make sure you have a valid SPF record that can be resolved into an effective list of IP addresses [from which emails are sent on your behalf]. Most of the tools below will do a quick SPF record validity check.
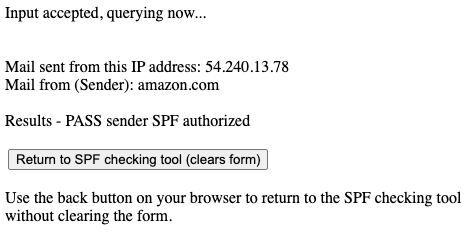
Test some specific emails to make sure that the sender IP addresses in the header fall within the range of IP addresses defined in your record. Here, you’ll want to actually send yourself some emails (to your personal GMail account) from your organizations services/servers. Once received in GMail, take a look at the headers and look for the sender IP address by looking for the line that begins with “Received: “. That line should show the originating IP address like below. The sending IP address below is 54.240.13.78 and the email was sent from [email protected].
Received: from a13-78.smtp-out.amazonses.com (a13-78.smtp-out.amazonses.com. [54.240.13.78]) by mx.google.com with ESMTPS id g11si6061992qko.4.2020.11.22.14.32.49 for <*YourEmailAddressWillBeHere*> (version=TLS1_2 cipher=ECDHE-ECDSA-AES128-SHA bits=128/128); Sun, 22 Nov 2020 14:32:50 -0800 (PST)
Here’s the results of testing email at the Kitterman site:
SPF Test Tools
Test your emails
For testing the overall email authentication success of your emails, see out knowledgebase article:
Test your SPF policies
Kitterman is the ‘OG’ SPF test tool : (although not super user-friendly)
Dmarcian does a good job of showing you the total number of lookups for each SPF entry (just expand your record to see)
MXToolbox is always great
Vamsoft has a detailed tester that works well with macros and UniversalSPF
Service-specific articles on SPF
Google Workspace (aka GSuite, Google Apps)
Microsoft 365 (aka Office 365)
Mailchimp (article is from Dmarcly)